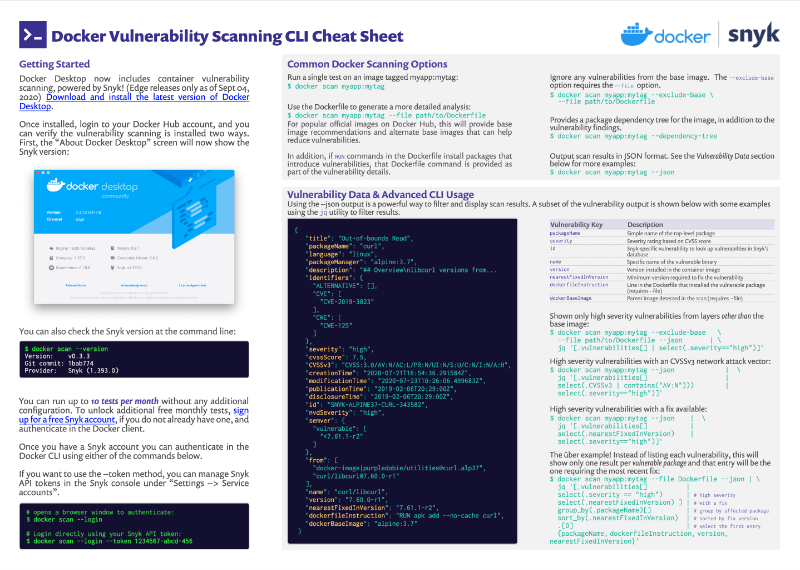
Snyk on Twitter: "Find vulnerabilities in container images and fix them before pushing the image to @Docker Hub or any other registry. #docker #security #snyk https://t.co/NDZyFqgOpY https://t.co/sh26Z9Yrre" / Twitter

JFrog and Docker Unveil Integrated Solution for Increasing Container Security & Developer Productivity

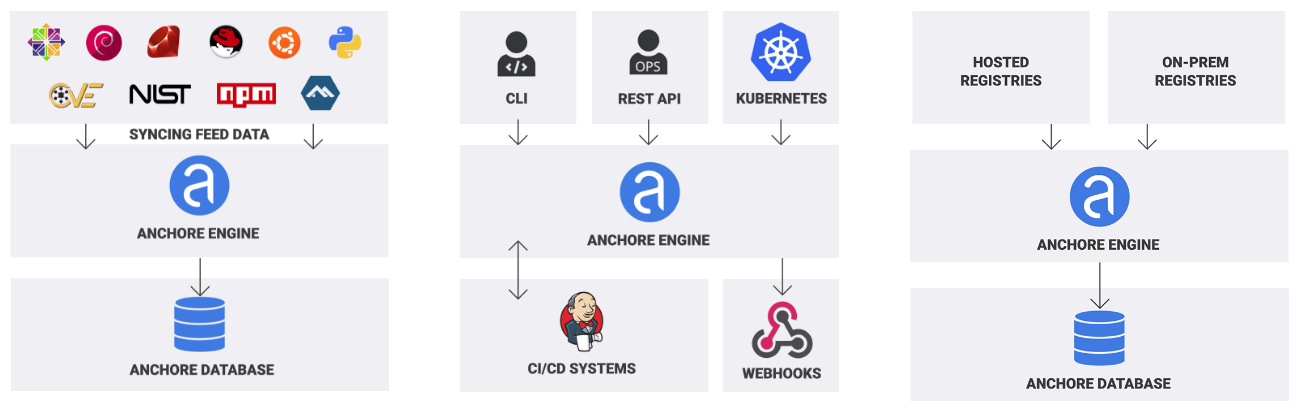
Introducing Container Image Scanning: Identify both misconfigurations and vulnerabilities with Bridgecrew

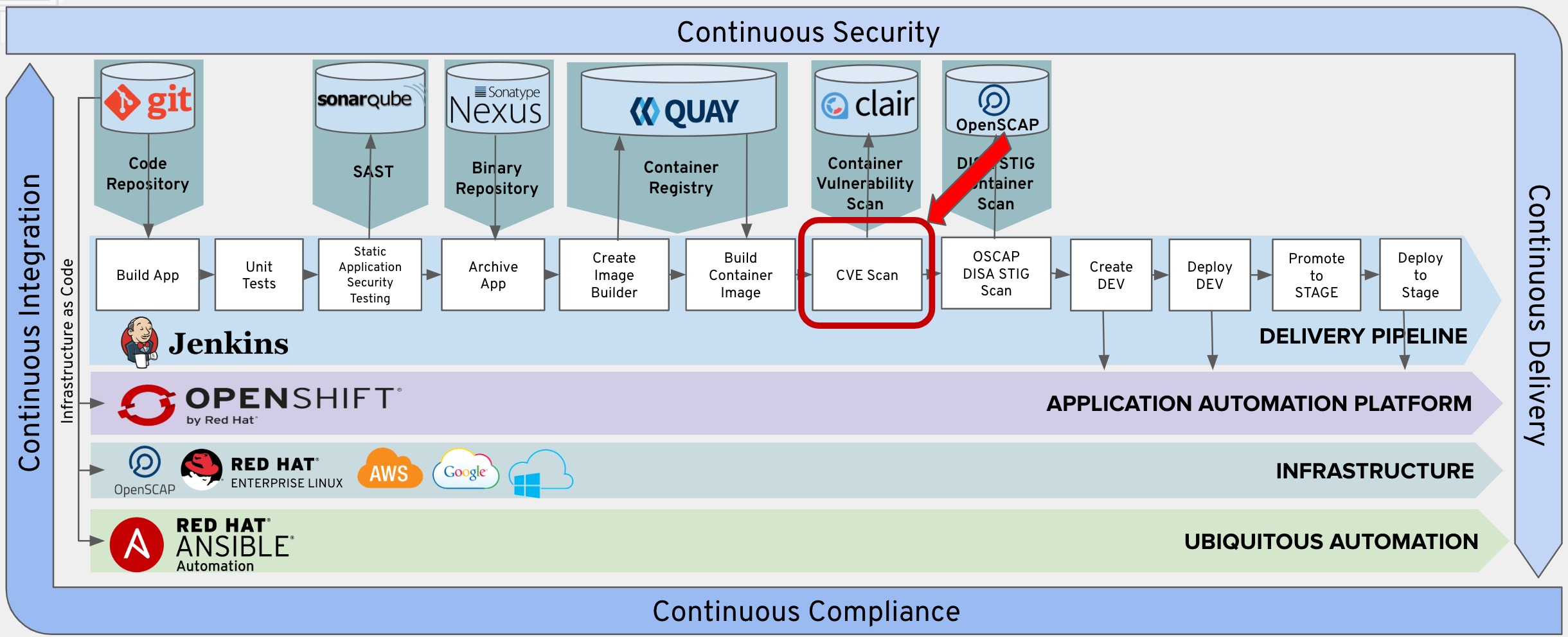
How to build a CI/CD pipeline for container vulnerability scanning with Trivy and AWS Security Hub | AWS Security Blog